Web application penetration testing helps to detect vulnerabilities and prevent cyber-attacks
Web application penetration testing is an effective way to detect vulnerabilities and prevent cyber-attacks. During penetration testing, techniques usually applied by attackers are used, and the application is analysed from the attacker’s point of view.
Who can benefit from web application penetration testing?
Any company that has a public website or develops web-based solutions for customers should conduct penetration tests at least once a year or upon completion of large-scale development projects to prevent cybercriminals from attacking and accessing their channels. Almost every company has a public website containing various simple functionalities such as a contact form, a feedback form, and a possibility for customers to submit enquiries or perform other business-related activities. Such functionalities are often a door through which an attacker can gain access to a company’s internal network.
Based on many years of experience in cyber security consultancy, we can say that there are mostly two types of clients who can gain the most benefit and confidence from web application penetration testing. These are companies that have a public website and companies that develop web-based solutions as a product.
Below, we will list the main misconceptions about web application security testing, which we would like to refute.
- Our website does not contain important functionality – there is only a contact form and the possibility to leave anonymous comments.
The website can still be vulnerable to critical security flaws such as cross-site scripting or injection attacks. As a result of these security flaws, an attacker can gain access to a web server or administrator accounts. What makes such security flaws particularly dangerous is that the initial access gained through them will, in turn, become a much more serious security flaw, enabling the attacker to take over the company’s entire internal network. - Our web server has little business value, and in the event of an attack, we can always restore the system from a backup and then upgrade it.
Having access to a web server is just the tip of the iceberg. It will enable the attacker to get their foot in the door and be one step closer to taking over the company’s entire network. Particularly dangerous are situations where the attacker gains access to personal data and user accounts through an attack on a web server. Such an attack will damage your company’s reputation and, as a result, you will lose the trust of your customers. - We have implemented a widely used content management system, so our website is secure.
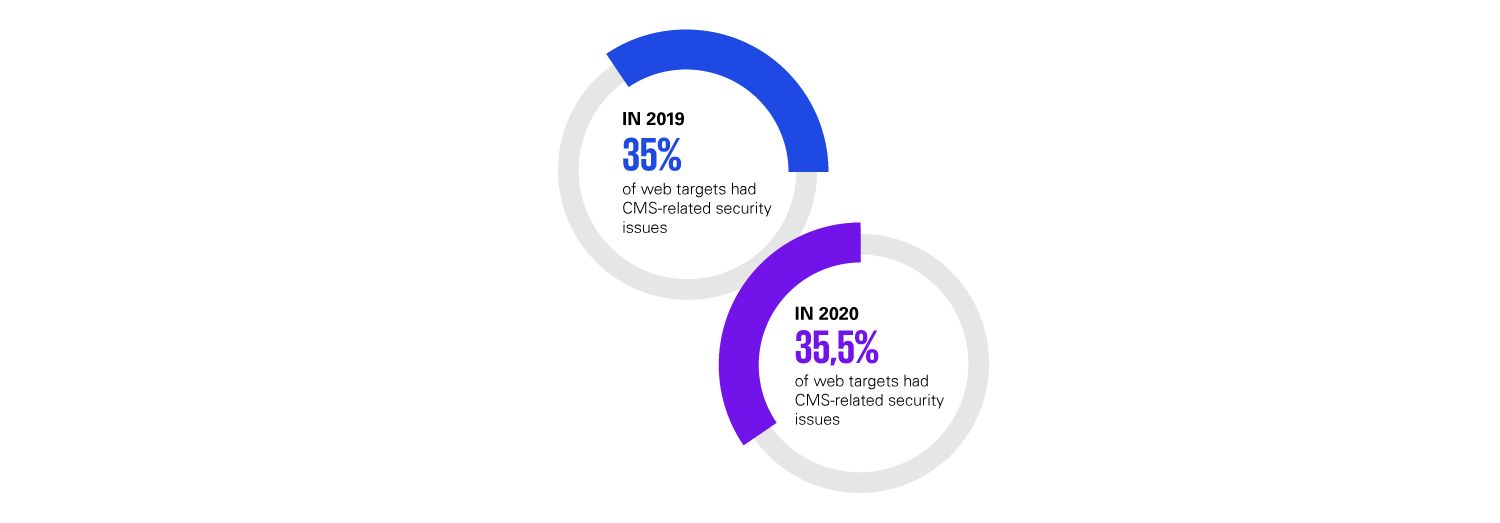
As soon as a new security flaw is detected in such a system, your website will become a very vulnerable target. Around 35% of web attacks are carried out against widely used content management systems such as WordPress and Joomla.
- We have outsourced the development and management of our website, and the service partner takes care of our company’s security.
Most security flaws in web applications occur accidentally, and most developers do not specialise in cyber security. For penetration testing, it is always better to use an independent third party who is an expert in the field. It is about the data and the well-being of your company, after all. - If you develop web-based solutions for your customers, it is not your company’s data or resources that are at risk but your reputation and quality of work. If you ensure the security of the solutions you have developed and penetration tests have verified this, you will prove to your customers that you are a reliable development partner. Ordering a penetration test from a globally renowned and trusted company is a strong quality label that will help to enhance your credibility.
How can the KPMG cyber security team help you?
Our cyber security experts can identify potential vulnerabilities that could allow attackers to exploit your application or website to their advantage. If you develop web-based solutions for third parties, we can use web application penetration testing to identify potential attack vectors and cyber security issues in your products, which you may not be aware of.
Our approach is flexible and client-driven, always complying with the requirements of the most appropriate security standards (OWASP ASVS). Our report includes an assessment of the overall cyber security quality, which includes a professional evaluation of the state of the tested web application from a cyber security perspective.
The following is a model assessment:
In addition to penetration testing, we look for bugs that, if fixed, will help to improve your web application's overall cyber security posture. To this end, we follow all cyber security best practices and standards (OWASP ASVS, CIS Benchmarks). As a result of this work, we will issue a detailed report containing a list of security flaws, recommendations on how to fix them and the order in which they should be fixed. Furthermore, when interacting with our experts, you can ask additional questions on how best to fix the bugs identified.
After the fixes have been implemented, we will perform a validation test to ensure that the fixes have been made correctly, they are effective and no new bugs have been created in the fixing process.
The Application Security Verification Standard (ASVS) has the following levels?
- Level 1 (Basic) – the minimum level suitable for all web applications;
- Level 2 (Standard) – the recommended level for most applications; this level is recommended when the application handles sensitive information, such as personal data, or involves business processes;
- Level 3 (Advanced) – suitable for critical systems, including applications related to the financial sector or critical systems in the military and public sectors.
All this sounds very expensive
The cost of web application penetration testing depends on the scope of the work, the functionality of the application and the security requirements you want to check your website against.
In most cases, the cost of a project ranges between 5,000 and 15,000 euros.
Please contact us for more information. We will map your current situation and find the best solution for your company or organisation.
Rein Luhtaru
Senior Cyber Security Specialist
rluhtaru@kpmg.com
Latest articles

Why Purple Teaming is the Missing Link in Modern Cybersecurity
In today’s cybersecurity landscape, most organizations are caught between two realities: they kn..

Reflections from the Field - A Red Team’s Perspective on Cybersecurity in Estonia
Over the past several years, our red team has conducted extensive offensive security assessments..
KPMG Expert: AI Solutions for Automating Routine Processes Deliver the Quickest Returns
By implementing artificial intelligence, the quickest returns are achieved thro..

KPMG IT Expert: Practitioner-Trainers Make Training Engaging and Practical
IT or cyber security training is more engaging when delivered by trainers who a..

Your Partners’ Weaknesses Can Affect Your Own Security
When planning your cyber defence strategy, it’s crucial to recognise that vulne..
Bolstering Cyber Resilience with High-Quality Red Teaming
The escalating complexity and frequency of cyberattacks pose a critical risk to the stability of f..
Turn threats into opportunities
Provide a safe and sustainable business environment for your company. We help build a resilient and reliable digital landscape, even in the face of changing threats.


KPMG Baltics OÜ
+372 626 8700cyber@kpmg.ee
Ahtri 4, 10151 Tallinn, Estonia
Contact us
${i18n('ask_more')}
Analysis of employee awareness
Analysis of employee awareness focuses on mapping the skills and increasing the competencies of the weakest link in cyber security: the users, the employees.
${i18n('ask_more')}
Threat assessment
Threat assessment is a tactical and technical service that allows a company to get a quick overview of external threats.
${i18n('ask_more')}
Maturity assessment
Maturity assessment helps plan IT investments and design further steps to mitigate vulnerabilities and ensure better security.